Introduction: Understanding Zero Trust Architecture As cyber threats continue to grow in complexity and frequency, organizations are re-evaluating their cybersecurity strategies. Zero Trust Architecture (ZTA) has emerged as a leading framework for securing networks by enforcing strict access controls and continuously validating trust. This article explores the principles of Zero […]
Cyber Security
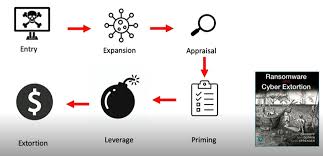
Introduction: The Evolving Ransomware Landscape As we move into 2024, ransomware continues to be a significant threat to organizations worldwide. Cybercriminals are increasingly sophisticated, utilizing advanced techniques to exploit vulnerabilities and extort money from businesses and individuals alike. This article explores the latest trends in ransomware attacks, the evolving threats […]
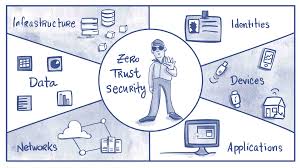
Introduction: Rethinking Cybersecurity In the face of evolving cyber threats, the traditional perimeter-based security model is proving inadequate. As we move through 2024, the Zero Trust security framework is gaining traction as a comprehensive approach to cyber defense. This model operates on the principle that no one—inside or outside the […]
Introduction: The Growing Threat of Ransomware As we progress through 2024, ransomware attacks continue to pose a significant threat to organizations across various sectors. These malicious cyber incidents not only disrupt operations but also jeopardize sensitive data and financial stability. With attackers employing increasingly sophisticated methods, understanding current trends and […]
Introduction Zero Trust Architecture (ZTA) has emerged as a critical security paradigm in 2024, focusing on the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter defenses, Zero Trust assumes that threats may exist both outside and inside the network. This approach emphasizes continuous verification, […]
Introduction As artificial intelligence (AI) technology advances, its applications in cyber attacks are becoming more sophisticated and threatening. In 2024, AI-driven cyber attacks are increasingly prevalent, leveraging machine learning and other AI techniques to enhance the effectiveness and stealth of malicious activities. This article explores how AI is being used […]
In 2024, the landscape of cyber security is continually shifting as new threats emerge and solutions evolve. As technology advances, so too do the tactics employed by cybercriminals. This article explores the latest threats facing organizations and individuals, examines the innovative solutions being developed to combat these threats, and provides […]
Ransomware-as-a-Service (RaaS) represents a significant evolution in the cybercrime landscape, making sophisticated ransomware attacks accessible to a broader range of malicious actors. This model has transformed ransomware from a tool used by skilled hackers into a commoditized service available to anyone with malicious intent. Here’s an in-depth exploration of the […]
Introduction This is a digital era in which everybody is using computer devices for all activities like business, studies, financial or economic management, data record and storage, processing of all personal or official tasks, etc. So this immense use of computer and technology is not only providing facilities and benefits […]
introduction This is the era of the 4th industrial revolution, and technology is evolving faster than ever. Now everyone is relying on computer devices, using software for their different types of activities, business, studies, all kinds of data records like property, hospitals, student, security records, even in every field people […]